Support for Your Privacy Risk Assessment Report
We want to provide context for how best to interpret your Privacy Risk Assessment Report. Your report provides insights for both privacy and cybersecurity risks.
Below, you will find general report details, or you can visit our tailored guidance specific to your use case
Privacy Risk Report Details and Definitions
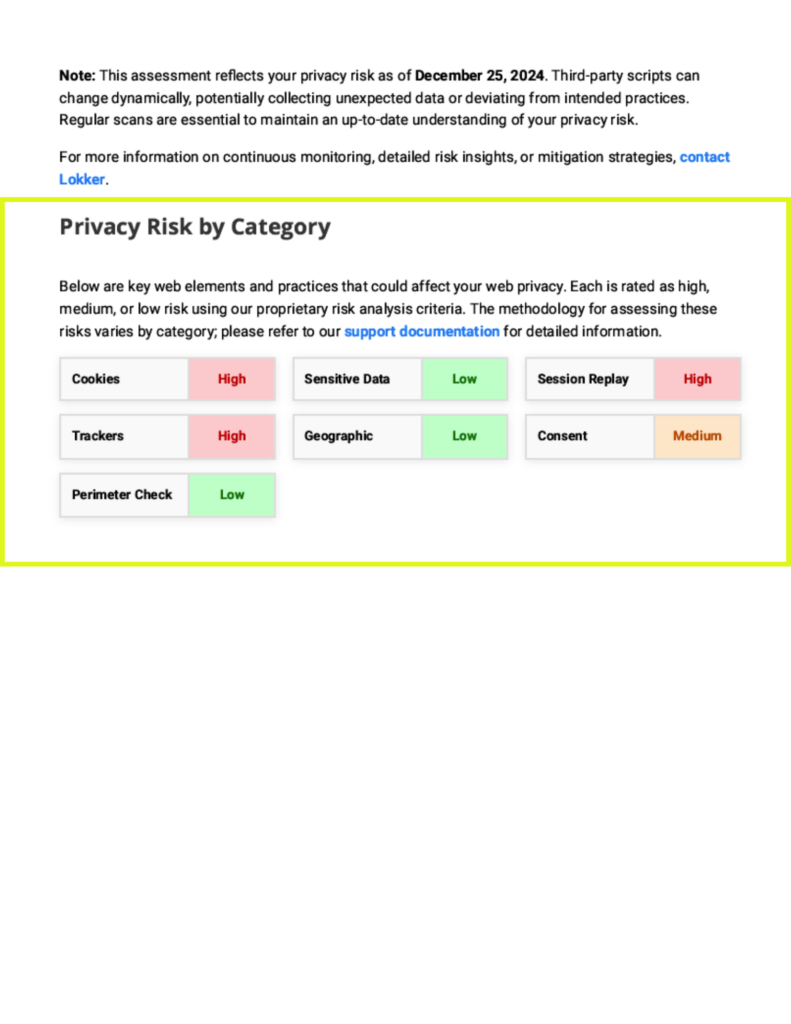
Privacy Risk by Category
Lokker’s Web Privacy Risk Score™ offers organizations a clear and quantifiable way to evaluate, identify and mitigate web privacy risks that may result in a privacy breach, enforcement action or lawsuit. This tool provides a detailed view of risks across website domains or portfolios of domains, allowing companies to pinpoint risks by webpage, severity, and frequency.
Lokker’s risk model uses advanced scanning capabilities to evaluate websites without requiring integration or code modifications. The baseline risk scores are based on an analysis of over 80,000 websites across various S&P industry sectors. The scoring model measures overall risks and breaks them down into seven specific categories described below.
Cookies
Cookies represent one of the most fundamental mechanisms for data sharing on websites. They can store user information that is later shared with or accessed by third parties. Risks in this category are identified under the following conditions:
- Third party cookies were set before obtaining explicit user consent. This practice can lead to data being shared with advertisers or other entities to track user behavior.
- Third party cookies were loaded without obtaining explicit user consent.
Data being stored in a third-party cookie indicates that data has been shared with a third party. As a result, the cookie can later be used to reference this data for showing ads to the user, merge with data shared from other sites or other online / offline transactions.
This category also includes:
- First party cookies that were set before or without obtaining explicit user consent.
First-party cookies are generally intended for website use, while third-party cookies are for use by third parties. However, a JavaScript workaround exists that allows third parties to set first-party cookies. This can create first-party cookie risk by enabling third parties to store user information using first-party cookies.
Why it matters:
Cookies facilitate data sharing between websites and third parties. This data can be used for targeted advertising, user profiling, or merging with other datasets, potentially exposing users to privacy violations.
Sensitive Data
This category evaluates the presence and sharing of sensitive user information, such as personally identifiable information (PII), financial details, or health-related data. The type of data being shared affects the risk score depending on the sensitivity of the data, as does the type of site and page factors on which it is found. For example, sending credit card data is more sensitive than sending the user’s first name.
How it’s assessed: Lokker tests for data loss by filling out forms with fake data, and then does a lookup to see if any of that data is sent to a third party, and if so, where did it go and to whom.
Why it matters:
Unauthorized sharing of sensitive data increases the risk of identity theft, fraud, and regulatory penalties under laws like GDPR or CCPA.
Session Replay
The session replay risk category includes session replay tools from third parties like Dynatrace or Hotjar being detected on a website. These tools record user interactions (e.g., clicks, keystrokes, and navigation) to help site owners understand user behavior. Risk occurs when data is being shared with these third parties, especially when the proper notice has not been given and/or the proper consent has not been received from the user. Improper notice or lack of user consent exacerbates privacy risks.
Why it matters: When sensitive user interactions are recorded and shared without consent, it can lead to significant privacy concerns and legal repercussions.
Trackers
This category assesses third-party tracking technologies embedded on your website, which can monitor user behavior and share data with external entities which you may not have approved for sharing. There are several types of risks:
Fingerprinting. Scripts taking a unique “fingerprint” of a user’s browser in order to track their activity across different websites.. Lokker looks at all of the methods called by a script and assigns a weighting to the ones commonly used for browser fingerprinting. The severity and number of methods used will impact the score.
Trackers detected. The presence, number and type of third-party code (Trackers) found on your site affects the score.
User Ids (keys) sent. Lokker assesses the data sent to a third-party to check if there is any high risk data like user_ids sent back to the third party.
User behavior sent. Lokker assesses the data sent to a third party to check if there is any sensitive behavior sent back to the third party. E.g. newsletter subscription provided by the user.
Third-party iframes found. This check looks for iframes created on your site by third parties. When these are found the risk score is increased accordingly because it is difficult for your site monitoring and logging systems to view activity within these iframes.
Why it matters:
Trackers can compromise user privacy and undermine trust by sharing data without user awareness or consent.
Geographic
This category evaluates the geographic location of third-party servers receiving data from your site. Some countries are considered high-risk due to their regulatory environment, cyber practices, or political climate.
High-risk countries:
Russia, China, Belarus, Venezuela, Cuba, Turkmenistan, Syria, Eritrea, North Korea.
How it’s assessed:
Lokker examines the IP addresses of third-party servers to determine their geographic location.
Why it matters:
Data sent to high-risk jurisdictions may be vulnerable to surveillance, hacking, or misuse, leading to significant privacy concerns.
Consent
This category examines whether your website complies with legal requirements for obtaining user consent. Checks include:
- Is the user presented with a privacy consent banner when they enter your site?
- Do the pages on your site have the regulatory message for ‘Do Not Sell My Information’?
If either of these are true, the score risk is increased.
Why it matters:
Failure to provide proper consent mechanisms can lead to legal penalties under privacy regulations such as GDPR and CCPA.
Perimeter Check
This category includes checks against the domain name used by any third-parties on your site and their associated risks.
Checks include:
Malicious Domains. Lokker cross reference check third-party requests against a malware database to identify risky domains.
Security certificate issues. Lokker evaluates if a third party is using a server without a functional security certificate. If not, the risk score is increased accordingly.
Domain registration age: Lokker identifies if domains were registered within the past 30 or 180 days.These could be higher risk, as an actor could register a new domain and use it before it could be flagged as malicious or be included onto session replay or risky third party lists.
Why it matters:
Newly registered domains or those with inadequate security measures can pose significant risks to user data and site integrity.
By breaking down privacy risks into these categories, Lokker’s Web Privacy Risk Score™ provides actionable insights to help organizations safeguard user data, enhance compliance, and build trust and integrity.
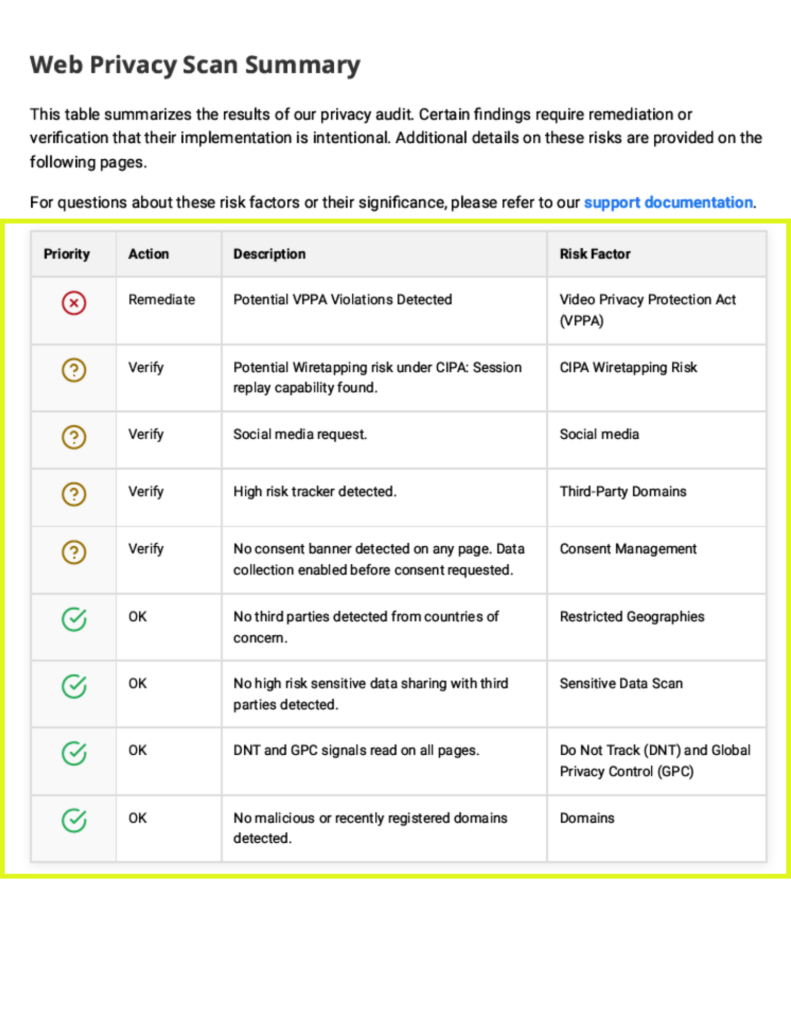
Understanding the Web Privacy Risk Summary
CIPA Wiretapping Risk
Why We Look for This
The California Invasion of Privacy Act (CIPA) prohibits wiretapping, which may occur when session replay tools record user interactions without proper consent. Having a session replay tool on your site, without 100% correct notice and consent creates privacy risk. Session Replay = Wiretapping tools.
How We Check for This
We scan your website to identify session replay tools and assess whether they are active or collecting data.
Understanding the Report Results
No session replay tools were detected.
No risk was identified.
Potential wiretapping risk under CIPA: Session replay capability found.
High risk. Confirm tools are disabled or ensure proper consent is collected.
Consent Management
Why We Look for This
Over 10 states and 120 countries around the world have consumer data privacy laws which impact if and how your business uses a consent banner.
How We Check for This
The Lokker scanner simulates a user going to your site and checks if a consent banner is presented on all the scanned pages.
Understanding the Report Results
Consent banner found on all pages.
No risk was identified.
No consent banner detected on >90% of pages. Data collection enabled before consent requested.
The majority of your pages are missing a consent banner. Data is being collected by one or more third parties prior to receiving consumer consent.
No consent banner detected on any page. Data collection enabled before consent requested.
A consent banner does not exist on your site. Data is being collected by one or more third parties without receiving consumer consent.
Domains
Why We Look for This
Malicious domains which contain malware can indicate privacy risk or a data breach.
Recently registered domains are considered risky because cybercriminals often use newly registered domain names to host malicious content like phishing sites, malware distribution points, or command-and-control servers. They are taking advantage of the fact that these domains lack an established reputation and can easily slip past security filters, making them a potential threat when the domain name of a tag on your site is a recently registered domain.
How We Check for This
Malicious Domains: We check third parties on your site against a database of known malicious sites.
Recently Registered Domains: We check the domain registration date of all third parties on your site.
Understanding the Report Results
No malicious or recently registered domains detected.
None of the third parties on your site is using a recently registered domain or a domain which has been flagged as malicious.
Third party malware or recently registered domains detected.
Recently registered domains or a domain which has been flagged as malicious has been detected. Take action to verify and remediate as needed.
Restricted Geographies
Why We Look for This
Tags on your site from servers in certain high risk countries, as designated by the US government, are considered high-risk due to their regulatory environment, cyber practices, or political climate.
How We Check for This
Lokker examines the IP addresses of third-party servers to determine their geographic location. is from any of these “Countries of Concern”:
– Russia, China, Belarus, Venezuela, Cuba, Turkmenistan, Syria, Eritrea, North Korea.
Understanding the Report Results
No third parties detected from countries of concern.
None of the third party tags on your site originate from a country of concern.
Restricted Geographies: Third parties detected from countries of concern.
Some of the third party tags on your site originate from a country of concern.
Sensitive Data Scan
Why We Look for This
Unauthorized sharing of sensitive data increases the risk of identity theft, fraud, and regulatory penalties under laws like GDPR or CCPA.
How We Check for This
Lokker tests for data loss by filling out forms with fake data, and then does a lookup to see if any of that data is sent to a third party, and if so, where did it go and to whom.
Understanding the Report Results
No high-risk sensitive data sharing with third parties detected.
High-Risk Data: Includes personal details such as name, address, email, phone number, credit card information, medical terms, and social security numbers.
Extremely sensitive data sent to third party.
Extremely Sensitive Data: Flags are triggered if passwords, credit card numbers, or SSNs are shared with third parties.
Social Media
Why We Look for This
When third party tags from some social media are used on healthcare sites, privacy risk is increased.
How We Check for This
If the site has been designated a healthcare site in the Lokker system configuration, then the Lokker scanner examines the site content to determine if any third party tags originate from Social media, e.g. Meta (Facebook/Instagram), TikTok, LinkedIn, Snapchat, or Pinterest
Understanding the Report Results
No social media domain requests detected.
The use of a social media tag on a healthcare site has not been detected.
Meta pixel found on a healthcare page.
Social media request on a healthcare site.
Meta and TikTok pixels found on a healthcare page.
Social media request.
The use of a social media tag on a healthcare site has been detected.
Third-Party Domains
Why We Look for This
This category assesses third-party tracking technologies embedded on your website, which can monitor user behavior and share data with external entities which you may not have approved for sharing. This can compromise user privacy and undermine trust by sharing data without user awareness or consent.
How We Check for This
We look for Fingerprinting. Scripts taking a unique “fingerprint” of a user’s browser in order to track their activity across different websites.. Lokker looks at all of the methods called by a script and assigns a weighting to the ones commonly used for browser fingerprinting. The severity and number of methods used will impact the score.
We consider the presence, number and type of third-party trackers found on your site.
We look for User Ids (keys) sent. Lokker assesses the data sent to a third-party to check if there is any high risk data like user ids being sent back to the third party.
We look for User behaviour being sent. Lokker assesses the data sent to a third party to check if there is any sensitive behavior sent back to the third party. E.g. newsletter subscription requested by the user.
We examine for the presence of Third-party iframes on your site. When these are found the risk score is increased accordingly because it is difficult for your site monitoring and logging systems to view activity within these iframes.
Understanding the Report Results
No High risk tracker detected.
None of the checks listed above were found to be true.
High risk tracker detected.
Trackers that have been identified as malicious or named in a lawsuit.
Significantly more 3rd party domains than S&P 500 average.
Having a large number of trackers on your site could indicate risk.
Video Privacy Protection Act (VPPA)
Why We Look for This
The Video Privacy Protection Act (VPPA) prohibits the disclosure of personally identifiable information about users’ video-watching habits without explicit consent. It is a federal law originally passed to protect people’s video rental histories. This law was passed in the late 1980s regarding VHS videotape rental history, but it has been repurposed by plaintiffs to file cases against companies. Due to the lack of statute clarity, there are multiple instances of plaintiff-led litigation referencing alleged VPPA violations.
How We Check for This
Consider this scenario: a consumer views a website with video content and the consumer’s video-watching behavior is shared with a third party without explicit consent. Lokker looks for combinations of events that lead to examples like these to help companies avoid these cases. We also analyze how these pixels are configured to see if they share sensitive video analytics, such as video titles or watch times, with third parties.
Understanding the Report Results
No VPPA Violations Detected
There are NO pages on your site with video content that is being shared with third parties without user consent.
Potential VPPA Violations Detected
There are ONE OR more pages on your site with video content that is being shared with third parties without user consent.
Understanding Critical Risk Remediation
Domain Hijacking
Domain hijacking is the unauthorized takeover of a domain name, usually by exploiting security weaknesses or administrative loopholes. Attackers gain control of a domain and can redirect traffic, disrupt services, or use it for malicious activities. Consequences of domain hijacking include:
- Traffic Redirection → Attackers redirect visitors to malicious websites.
- Brand Reputation Damage → Users may lose trust in the hijacked domain.
- Email Spoofing & Phishing → Cybercriminals can send fake emails from the hijacked domain.
- Data Theft → If the domain hosts a website, user data may be compromised.
- Financial Loss → Ransom demands or loss of business due to website downtime.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Spread | This is the number of scanned pages(20) and the number of pages on your site(3) with this risk was found. | Found on 3 of 20 pages inspected |
Description | This is the act of changing the registration of a domain name without the permission of its original registrant. | Domain Hijacking |
Example Page | This is an example of a page with a hijacked domain. There may be additional pages with risk. | https://farrelldistributing.com/rtd-cocktails |
Example Request URL | The complete URL of the third party which has hijacked this page. | https://polyfill.io/v2/polyfill.min.js?features |
Count | Number of pages where this risk was found | 3 |
Pages Impacted | The names of one or pages on your site where this risk was found. | https://example.com/beer/
|
Extremely Sensitive Data Sent to Third Party
Lokker performs checks to prevent the sharing of highly sensitive data with third parties. This includes personal information such as passwords, social security numbers, and credit card information, which can be used to compromise an individual’s privacy or commit identity theft.
| Attribute | Additional Information | Description |
|---|---|---|
| Risk | Critical is the highest level of risk. | Critical |
| Spread | This is the number of scanned pages (20) and the number of pages on your site (1) with this risk found. | Found on 1 of 20 pages inspected |
| Description | Extremely sensitive data has been shared with a third party, including passwords, credit card numbers, or social security numbers. | Use extreme caution when collecting and sharing this information. Review your agreement with this partner to ensure appropriate security measures. If unsure, block data sharing via the Manage Third Parties dashboard. |
| Field | This identifies the type of data shared. | Password |
| Domain | The third-party website receiving the data. Engage your engineering team to understand why. | formstack.com |
| Script | When a script is used to share data, this shows the user action that initiates the sharing. | Button Click |
| Target URL | The URL of the third-party website receiving the data. | https://eternityweb.formstack.com/forms/index.php |
| Fake Data Field | Lokker simulates a “fake” user entering data on your site for testing. | orBOxAAzW6d@Ejm7 |
| Example Page | An example of a page where sensitive data is sent to a third party. | https://farrelldistributing.com/rtd-cocktails |
| Count | Number of pages where this risk was found. | 1 |
| Pages Impacted | Names of the pages on your site where this risk was found. | https://farrelldistributing.com/request-a-donation |
Meta Pixel Found on Healthcare Page
This risk occurs when a pixel from Meta is placed on a page that provides health care information to the user.
The Meta pixel, when placed on a webpage that displays healthcare information, sends data to Facebook. This data includes the Facebook user ID and details of the page viewed. Because Facebook also has access to email addresses and other personal information, it can link a real person to the specific healthcare information viewed. As a result, Facebook gains knowledge of the user’s healthcare interests or conditions.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Spread | This is the number of scanned pages(20) and the number of pages on your site(3) with this risk was found. | Found on 3 of 20 pages inspected |
Description | While this risk is referred to as the Meta Pixel risk, it is the Facebook website that is receiving information from your site. | We detected the Meta Pixel on the page, on a website we believe to be in a higher risk industry. |
Industry | Healthcare | Medical Devices and Supplies |
Example Page | This is an example of a page on your site with the Facebook pixel. There may be additional pages with risk. | https://blueskybio.com/pages/bio-cut |
Example Request URL | The complete URL of the third party which is receiving information from your site. | https://www.facebook.com/tr/?id |
Meta Pixel ID | Facebook uses this Id to identify the user. | 232570173945555 |
Count | Number of pages where this risk was found | 3 |
Pages Impacted | The names of one or pages on your site where this risk was found. | https://example.com/pages/about-us |
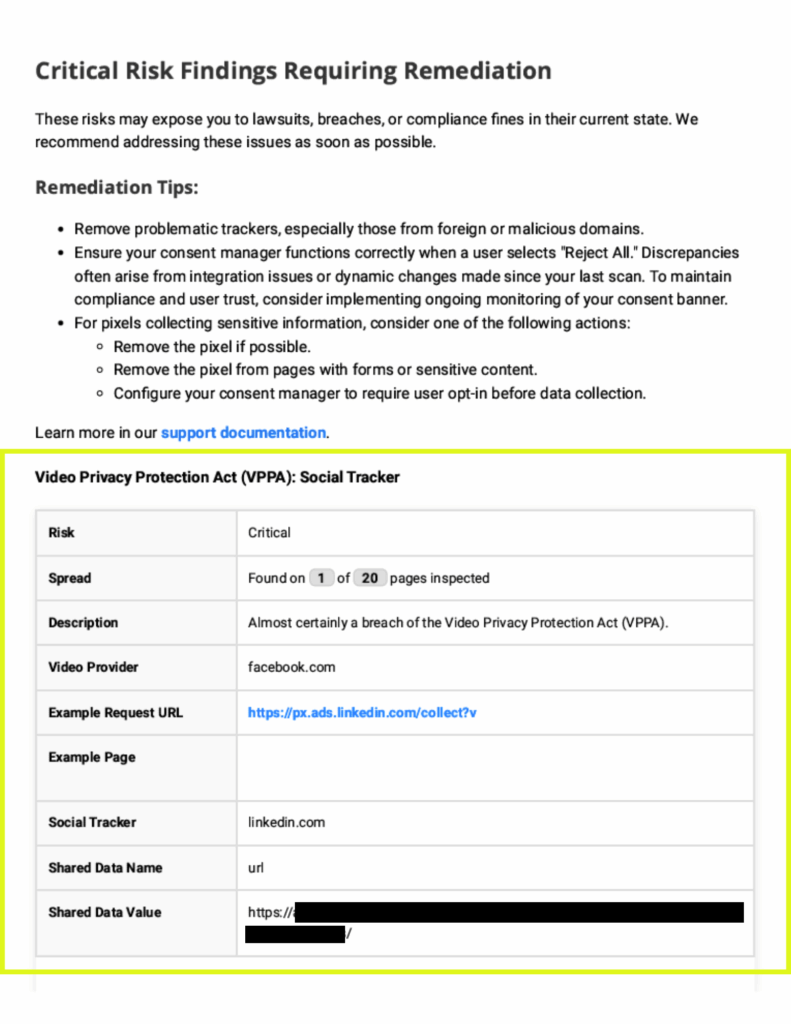
Potential VPPA Violations Detected
The Video Privacy Protection Act (VPPA) risk arises when a website with playable video content shares user data with a third-party that possesses personally identifiable information (PII) of those users. This creates a privacy risk as the third party can then associate specific individuals with their video viewing habits. The VPPA risk occurs when 3 conditions simultaneously exist:
- Website with Video Content: The first condition for VPPA risk is the presence of a video on a website that users can play or that plays automatically. This video content triggers the potential for data sharing and privacy concerns.
- Data Sharing with Third Party: When a user interacts with the video content, the website may send data to a third-party platform (e.g., social media, analytics provider). This data transfer can include information about the user’s activity on the page, potentially identifying them as having viewed the video.
- Third Party Possesses PII: The third-party receiving the data possesses PII of the user, such as their email address or other identifying information that “identifies a person”. This PII, combined with the video viewing data, enables the third party to create a profile linking specific individuals to their video viewing behavior.
The legal risk exists because the third party gains knowledge of the email addresses (or other PII) of individuals who had access to the video on the website. This can be a significant privacy breach, as it allows the third party to associate specific people with their video viewing habits. In a legal action, the website owner could be held responsible for enabling this breach by allowing the third-party tracking on their site.
Key points for preventing this risk include:
- User Awareness: Users may not be aware that their video viewing activity is being shared with third parties and linked to their PII. This lack of transparency raises privacy concerns.
- Data Control: The website owner has a responsibility to control the data that is shared with third parties and to ensure that user privacy is protected.
Compliance: Websites that include video content must be mindful of VPPA compliance and take steps to mitigate the risk of data sharing and privacy breaches.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Spread | This is the number of scanned pages(20) and the number of pages on your site(1) with this risk was found. | Found on 1 of 20 pages inspected |
Description | VPPA is the law which could be used to bring legal action. | Almost certainly a breach of the Video Privacy Protection Act (VPPA). |
Example Page | This is an example of a page containing the video and a tag which shares data. There may be additional pages with risk. | https://example.com/2023/02/08/drayage/ |
Video Provider | Hosting website of the video found on the page. | facebook.com |
Example Request URL | The complete URL of theThird Party which is informed that the user is on a page with a video. | |
Social Tracker | Third Party which is informed that the user is on a page with a video. | linkedin.com |
Shared Data Name | Parameter used in the URL sending information to a third party or “URL” if no data name is used. | |
Shared Data Value | The value of the data being shared. | tiitanic – (px.ads.linkedin.com/collect?video=titanic) |
Count | Number of pages where this risk was found | 1 |
Pages Impacted | The names of one or pages on your site where this risk was found. | https://example.com/2023/02/08/drayage/ |
GPC
The Global Privacy Control (GPC) is a setting that can be enabled within a user’s web browser. When active, it transmits a signal to websites when a user visits the site. This signal communicates the user’s preference for privacy, indicating that their personal data should not be sold or shared with third parties, except when necessary to provide the requested service.
The GPC signal is intended to streamline the process of exercising privacy rights online. By enabling GPC, users can avoid having to manually adjust their privacy settings on each website they visit. Instead, the GPC signal automatically conveys their privacy preferences to websites that recognize and honor the signal.
The mechanism for honoring Global Privacy Control (GPC) on a website is typically the consent banner system as most consent banner systems can be configured to honor GPC signals. GPC signals may be ignored if this system is not configured correctly, which creates risk.
Lokker detects if your website is honoring the GPC signal. If your website is not respecting GPC, it is flagged here. There are potential legal and regulatory actions for this including fines, penalties, and lawsuits. Additionally, your company could face reputational damage, loss of customers, and increased scrutiny from regulatory bodies. In severe cases, there could be criminal charges and imprisonment for individuals responsible for the non-compliance.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Page Count | This is the number of scanned pages(20) and the number of pages on your site(3) with this risk was found. | Found on 3 of 20 pages inspected |
Example Page | This is an example of a page which is not checking for GPC. | https://example.com/careers |
Example Request URL | The complete URL of the page which is not checking for GPC. | https://polyfill.io/v2/polyfill.min.js?features |
Count | Number of pages where this risk was found | 3 |
Sensitive Data Sent to Third Party
Lokker checks to ensure that sensitive data is not being shared with a third party. This type of data includes elements like: first name, middle name, last name, full name, password, email address, company name, phone number, credit card, street address, state, city, country, zip, sex, diagnosis, credit card name, credit card expiry month, credit card expiry year, credit card expiry, or age. This type of personal information data can be used to expose an individual’s private information or help steal their identity.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Spread | This is the number of scanned pages(20) and the number of pages on your site(1) with this risk was found. | Found on 1 of 20 pages inspected |
Description | Sensitive data has been shared with a third party. This includes any of the following information: First name, middle name, last name, full name, password, email address, company name, phone number, credit card, street address, state, city, country, zip, sex, diagnosis, credit card name, credit card expiry month, credit card expiry year, credit card expiry, or age.
| Use extreme caution when collecting and sharing this information with a third-party. Review your agreement with this partner to ensure they have appropriate security measures to keep this data private and safe, as a data leak could have severe consequences for the subject, including possible identity theft or fraud. If you don’t recognize the partner receiving the data or have yet to be able to verify their security practices are sufficient measures, block data sharing with this partner through the Manage Third Parties dashboard for partners that are subscribed to Lokker Privacy Edge. |
Field | This identifies the type of data which has been shared. | State [the user resides in] |
Domain | Here we can see the third party website receiving the data. It is recommended to engage your engineering staff to understand why this third party is receiving this data. | formstack.com |
Script | When a script is used to share data, this contains the user action which initiates the sharing. | Button Click |
Target URL | Here we can see the URL of the third party website receiving the data. | https://eternityweb.formstack.com/forms/index.php |
Fake Data Field | Lokker simulates a “fake” user to your site which enters fake data in places on your site where data is collected. This is the fake data used on your site. | Alaska |
Example Page | This is an example of a page where extremely sensitive data is sent to a third party. There may be additional pages with this risk. | https://example.com/rtd-cocktails |
Count | Number of pages where this risk was found | 1 |
Missing Consent Banner
Lokker checks page to assure a consent banner is displayed. This report indicates a consent banner is missing on one or more pages. Having a privacy consent banner on your site is crucial for several reasons:
- Legal Compliance: More than 120 countries and 15 US states have data protection laws that require websites to obtain explicit consent from users before collecting and processing their personal information. A privacy consent banner ensures that your website complies with these legal requirements and avoids potential fines or legal action.
- Transparency and Trust: A privacy consent banner demonstrates transparency and respect for user privacy. It clearly communicates to users what data is being collected, how it will be used, and gives them the choice to consent or decline. This fosters trust and builds positive relationships with your website visitors.
- User Control: A privacy consent banner empowers users to control their personal data. It allows them to make informed decisions about whether or not they want to share their information with your website. This enhances user experience and gives them a sense of control over their online privacy.
- Data Protection: By obtaining explicit consent through a privacy consent banner, you can ensure that you are collecting and processing user data in a lawful and ethical manner. This helps protect user privacy and reduces the risk of data breaches or misuse.
- Brand Reputation: Respecting user privacy and demonstrating compliance with data protection laws through a privacy consent banner can enhance your brand’s reputation. It shows that you value your users and their privacy, which can attract more visitors and customers to your website.
Overall, a privacy consent banner is an essential element of a website that values user privacy and complies with data protection laws. It is a simple yet powerful tool that can help you build trust, enhance user experience, and protect your brand’s reputation.
Attribute | Additional Information | Description |
Risk | Critical is the highest level of risk. | Critical |
Page Count | Number of pages where this risk was found | 20 |
Example Page | This is an example of a page which is missing a consent banner. | https://example.com/careers |
Count | Number of pages where this risk was found. | 20 |
Understanding Verification Risks
Risks that have been identified as requiring additional information from you to verify the risk to your company.
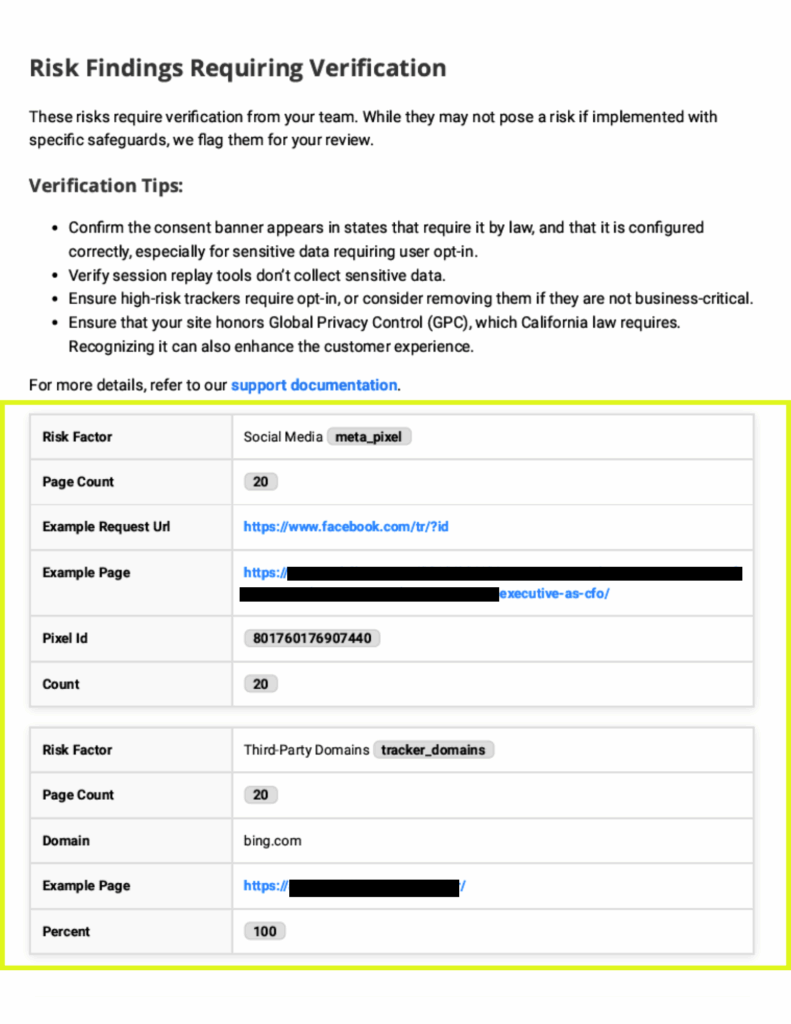
Social Media Domain
This risk assessment indicates that a social media website is currently receiving data from a specific page on your website. This data has been classified by Lokker as containing sensitive consumer Health Care information. Several US states, e.g. Washington, have explicitly blocked this type of data sharing. The transmission of this data to an external social media site raises concerns around data privacy and potential non-compliance with relevant healthcare regulations.
Attribute | Additional Information | Description |
Risk Factor | Verification is the second highest level of risk. | Verification |
Spread | This is the number of scanned pages(20) and the number of pages on your site(20) with this risk was found. | Found on 20 of 20 pages inspected |
Description | A social media third party tag was found on a page on your site with consumer health care information. | Social Media Domain Critical |
Industry | This indicates the industry classification of the page on your site with the risk. | Medical Devices and Supplies |
Example Page | This is an example of a page containing healthcare information and a tag which shares data. There may be additional pages with risk. | https://blueskybio.com/pages/cache-test |
Example Request Domain | Hosting website of the video found on the page. | facebook.net |
Example Request URL | Third Party which is informed that the user is on a page with a video – complete URL | https://connect.facebook.net/en_US/all.js#appId |
Social Media Site | Third Party which is informed that the user is on a page with a video. | |
Count | Number of pages where this risk was found | 20 |
Pages Impacted | The names of one or pages on your site where this risk was found. | https://example.com/pages/about-us |
Third-Party Domains
Lokker detects the number of third-party domains on websites and compares the overall number and type to the S&P 500 and other industries to determine if a website is better, comparable, or significantly worse than the baseline. These third parties increase the need for you to monitor for unauthorized data collection and proper governance. Often, third parties are not placed by you directly but are instead piggybacking on another script. The website owner remains responsible, even if they didn’t directly place the script themselves.
Attribute | Additional Information | Description |
Risk Factor | Verification is the second highest level of risk | Third-Party Domains tracker_domains |
Page Count | Number of pages where this risk was found. | 20 |
Domain | Hosting website of the video found on the page. | adnxs.com |
Example Page | This is an example of a page with one or more third party domains used for sharing data with the third party. There may be additional pages with this risk. | https://example.com/blog/why-automate/ |
Percent | The percent of pages on your site containing third party domains. | 100 |
CIPA Wiretapping Risk
session_replay_domains
The California Invasion of Privacy Act (CIPA) is a state law that safeguards the privacy rights of California residents by imposing strict regulations on the recording and monitoring of conversations and communications. This law applies to a broad range of mediums, including but not limited to telephone conversations, in-person discussions, and electronic communications. When third party session replay tools are used on a website, data sent to the third party enables it to know all the actions the user has taken on the web site. The user actions are effectively recorded. HotJar and Dynatrace are examples of session replay tools. The key provisions of CIPA include:
- Consent: CIPA generally mandates that all parties involved in a communication must provide consent before any recording can take place.This consent must be explicit and cannot be assumed or implied.
- Notice: In situations where recording is permissible, CIPA may require that parties be given clear and conspicuous notice that the communication is being recorded.
- Scope: The law’s scope extends beyond private conversations to encompass communications in public spaces and workplaces, provided that there is a reasonable expectation of privacy.
- Penalties: Violations of CIPA can result in severe consequences, including civil lawsuits for damages, injunctions, and potentially criminal prosecution.
Businesses operating in California or interacting with California residents must be particularly mindful of CIPA’s requirements. Failure to comply can lead to legal action, reputational damage, and financial loss. Companies should implement clear policies and procedures for obtaining consent, providing notice, and handling recorded communications. Businesses must be mindful of compliance measures needed on your website that go along with adding a sessions replay tool to your site.
Attribute | Additional Information | Description |
Risk Factor | Verification is the second highest level of risk | CIPA Wiretapping Risk session_replay_domains |
Page Count | Number of pages where this risk was found. | 20 |
Domain | Hosting website of the session replay too found on the page. | clarity.ms |
Example Page | This is an example of a page with one or more third party domains identifying session replay tools. There may be additional pages with this risk. | https://backbox.com/blog/eight-rules-of-backup/ |
Percent | The percent of pages on your site containing session replay tools. | 100 |
High Risk Tracker Detected
This assessment checks for the presence of any of the following tags which have been identified as high risk:
adnxs.com, bing.com, addthis.com, sharethis.com, bluekai.com
Attribute | Additional Information | Description |
Risk Factor | Verification is the second highest level of risk | Third-Party Domains tracker_domains |
Page Count | Number of pages where this risk was found. | 20 |
Domain | Hosting website of the high risk third party found on the page. | adnxs.com |
Example Page | This is an example of a page with one or more third party domains identifying session replay tools. There may be additional pages with this risk. | https://example.com/2023/09/05/acertus-acquires-rcg-logistics/ |
Percent | The percent of pages on your site containing session replay tools. | 100 |
Take Action on Your Privacy Risks Today
Need more details? If you have questions or want a deeper analysis, reach out—we’re happy to help.
- Fix Privacy Issues Fast: We’ll identify and resolve risks from your report.
- Stay Protected: Ongoing monitoring keeps your site secure.
- Simplify Compliance: Upgrade consent management for a seamless, law-compliant experience.
Don’t wait—secure your site and protect your reputation today.
Additional Privacy Resources
Explore the latest trends, tips, and insights in our world. Get the knowledge to empower your business growth and increase productivity.